| Storage sharing and read only | KernSafe iSCSI SAN User Manual |
In most of the time, using iSCSI Target such as KernSafe iSCSI SAN as the storage server to let many clients share one hard disk, partition, image file or security image file can share and utilize the storage resources to the largest extend and are convenient for centralized management. For data updates, update the target once and for all. However, according to the principle of storage, multiple clients’ sharing for read-write of one storage device (LUN) would bring risks to data corruptions, which is mainly due to the following reasons:
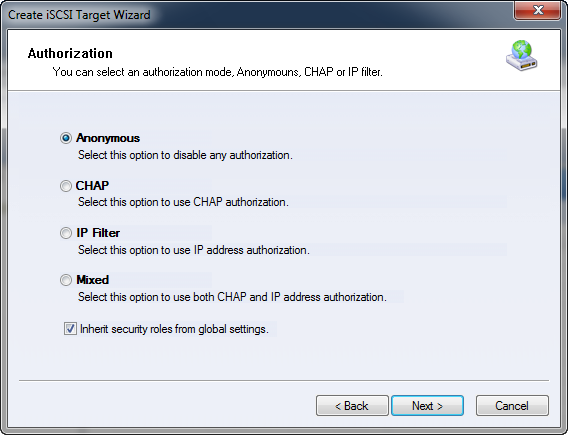
Therefore, KernSafe iSCSI SAN provides a read-only mechanism with separate permissions, read-only access for a part of users (initiators) and complete read-write access for another part of users. This prevents the data corruption caused by term 1 and 2. For users with complete read-write access, KernSafe iSCSI SAN normally allows only one user can log in, which eliminates the possibility of data corruption caused by the concurrent data writing of multi-users. When creating the Target, it can be controlled by Anonymous, CHAP, IP Filter or Mixed verification as shown in figure 1.
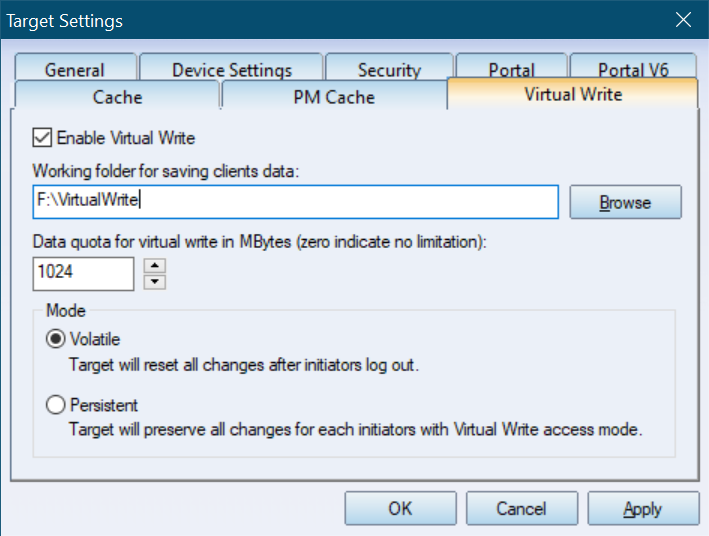
Virtual write
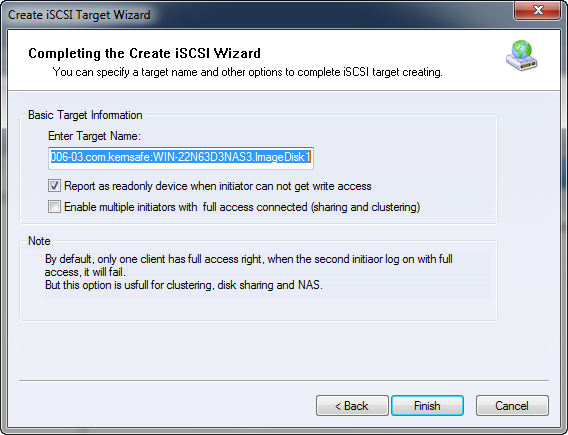
Note: When using this function, do not check "Report as read only device when initiator can not get write access" while creating Target as shown in figure 3.
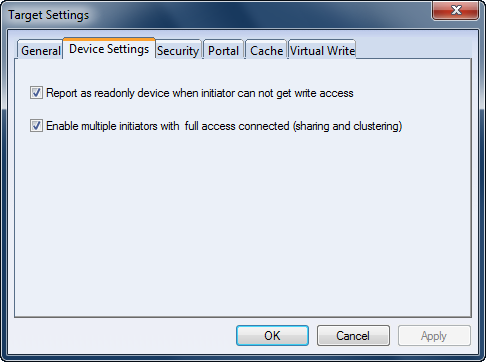
Concurrent writing of multi-users mentioned above may lead to the data corruption. But when your storage server is running in the environment of cluster, the function of concurrent writing of multi-users is needed and the writing synchronization control is realized by cluster software. Thus, you only need to check “Enable multiple initiators with full access connected (sharing and clustering)” in the last page of Create Target Wizard as shown in figure 4.
|
|
SUPPORT
- Forum
- Support Ticket
- [email protected]

- Voice Mail:
- +1 (518) 289-4888